Emerging AI Threats: The Silent Risk of Acoustic Attacks
Written on
Chapter 1: The Rise of AI-Driven Acoustic Attacks
In today's digital landscape, concerns surrounding cybersecurity are escalating. A new and alarming threat has surfaced, one that operates quietly yet is strikingly precise. British researchers have harnessed artificial intelligence to create a deep learning model capable of deciphering keystrokes with an astonishing accuracy rate of up to 95%. This form of acoustic assault can be executed using merely a microphone, presenting substantial risks to both individual and corporate data integrity.
The Role of AI in Acoustic Threats
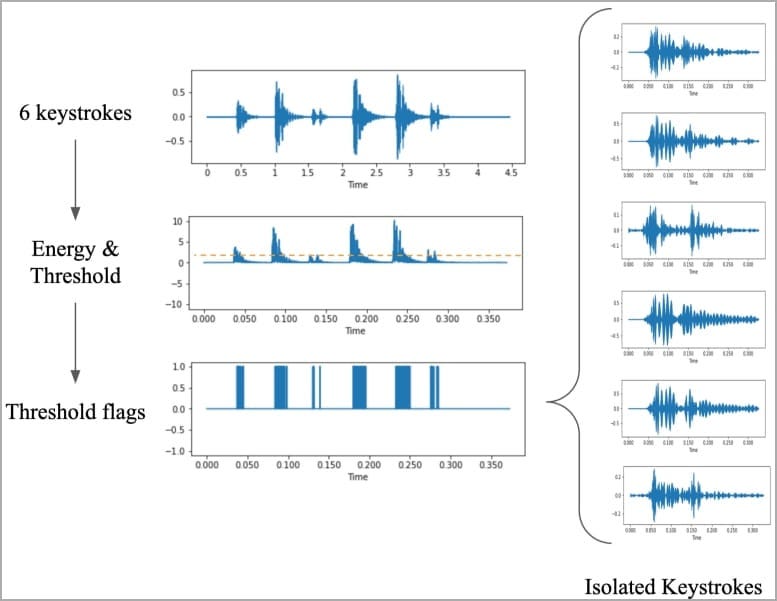
What distinguishes this novel attack is the integration of artificial intelligence. Thanks to deep learning algorithms, researchers achieved an extraordinary level of precision. The model was trained on recordings of 36 keys from a MacBook Pro, with each key being pressed 25 times. This data was then analyzed against their respective sound waveforms and spectrograms, enabling visual recognition of each keystroke.

How Significant Is the Threat?
The danger posed by this technology is both real and immediate. Whether a microphone is positioned close to a keyboard or keystrokes are captured during a Zoom meeting, the model's accuracy remains impressively high. In scenarios involving remote audio attacks via Zoom, the accuracy only declines slightly, to 93%. This indicates that an assailant could be nearby or virtually present in a call, successfully executing this acoustic assault. The potential consequences range from the theft of passwords and credit card details to the interception of private discussions.
Mitigation Approaches
Despite the notable threat, there are strategies to reduce risks. Potential solutions include:
- Utilizing completely silent keyboards
- Disabling microphones while entering sensitive information
- Employing virtual keyboards that scramble keystrokes, a practice already adopted in countries like Korea for secure accounts
Questions to Consider
As AI enhances the precision of acoustic attacks, should we prioritize 'acoustic security' within the cybersecurity framework?
With the advancement of AI, how can we effectively regulate its application in potentially damaging scenarios such as these attacks?
What measures can we take to better inform users about these unconventional security risks, and what proactive actions can they implement?
Final Thoughts
As technology continues to permeate every facet of our lives, the threats we encounter also evolve. Acoustic attacks, now amplified in accuracy through AI, serve as a stark reminder of this progression.
Stay informed about the latest developments in digital security to safeguard yourself effectively. Remain vigilant and prioritize your safety!
British researchers unveil an AI model that can decode keystrokes, presenting new cybersecurity challenges.
A quick overview of AI's impact on data security and the emerging risks associated with acoustic attacks.