# Understanding the MITRE ATT&CK Framework for Cybersecurity
Written on
Chapter 1: Introduction to the MITRE ATT&CK Framework
If you're new to the field of cybersecurity, you've likely encountered the MITRE ATT&CK framework. While you may have a rudimentary grasp of it, a comprehensive understanding of its mechanics and applications in security operations might still elude you.
Reflecting on my journey in cybersecurity over the past two years, I remember when my manager first suggested integrating the ATT&CK framework into our security operations. This prompted me to research the framework, leading to the realization that it serves as a vital resource outlining the tactics, techniques, and procedures (TTPs) employed by adversaries. The goal? To empower organizations to create what is known as threat-informed defenses.
As I delved deeper into the framework, I began to recognize its value while evaluating various Next-Gen Antivirus (NGAV) solutions. To my surprise, I found that many products’ core functionalities were grounded in the ATT&CK framework, mapping suspicious or malicious activities to specific ATT&CK techniques. This revelation sparked my desire to fully grasp the framework and its practical applications for enhancing our defensive strategies.
In my quest for knowledge, I searched extensively for training on the MITRE ATT&CK framework. Unfortunately, I found limited free resources, mostly webinars that addressed specific applications rather than comprehensive training. However, I was thrilled to learn about MITRE's collaboration with Cybrary, which offered free courses for the MITRE ATT&CK Defender certification. This certification is a fantastic opportunity for professionals to showcase their expertise in this widely utilized framework, and I’m eager to pursue it.
What is the MITRE ATT&CK Framework?
As previously noted, numerous security products now incorporate the ATT&CK framework to correlate activities within an organization to specific adversary techniques. The driving force behind this integration is the concept of threat-informed defense.
Utilizing this framework allows security teams to better understand the tactics and techniques that adversaries employ, ultimately leading to more informed defensive measures. So, what does ATT&CK stand for? It represents Adversarial Tactics, Techniques, and Common Knowledge. In essence, MITRE describes it as “a knowledge base of adversary behaviors.”
Developed in 2013, the ATT&CK framework has evolved through contributions from security professionals who share insights from real-world incidents. This crowd-sourced nature makes it one of the most reliable frameworks available for security operations. Unlike many theoretical frameworks, ATT&CK is customizable and provides a comprehensive view of security gaps, which facilitates actionable improvements.
The Pyramid of Pain
You may have encountered David Bianco's Pyramid of Pain, which MITRE uses to illustrate the challenges adversaries face when certain indicators are blocked.
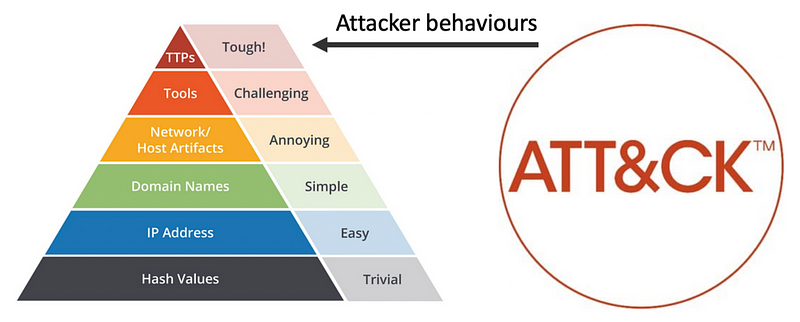
Blocking a hash? That's trivial for attackers. An IP address? Still manageable. Domain names? Annoying, but not insurmountable. As we ascend the pyramid, the indicators become increasingly specific, with TTPs being the most challenging for adversaries to circumvent if successfully blocked.
This highlights the importance of the ATT&CK framework in enhancing defenses against targeted attacks. Merely blocking known indicators of compromise (IOCs) isn't sufficient; attackers are adept at adapting their strategies. The ATT&CK framework guides us in fortifying our defenses by emphasizing the need to prevent not just known malicious IOCs, but also the behaviors associated with adversaries and their malware.
The framework comprises four components:
- Tactics - Explaining the motivations behind adversary actions.
- Techniques - Detailing how adversaries execute their actions.
- Sub-techniques - Offering a more granular view of adversary behaviors, often specific to platforms.
- Procedures - Illustrating specific methods adversaries use for a technique or sub-technique.
Together, these elements create a roadmap for assessing the effectiveness of a security operations program in defending against identified adversary behaviors.
Applying the Framework
Experts frequently emphasize that the ATT&CK framework isn’t a cure-all. It won't resolve issues within your Security Operations Center (SOC) by itself; its efficacy hinges on proper application.
A thorough assessment of your SOC's capabilities using the ATT&CK framework is essential, followed by ongoing efforts to enhance defenses and make informed decisions. When applied effectively, the ATT&CK framework aids in identifying gaps in data sources, detection capabilities, and mitigation strategies against known TTPs.
MITRE defines three crucial terms:
- Data sources - Information collected by sensors or logging systems that aid in detecting behaviors.
- Detections - The interpretation of collected data, constituting a high-level analytical process.
- Mitigations - Defensive measures that thwart the success of a technique.
Together, these elements help organizations categorize their data sources, improve detection methodologies, and ideally, fully mitigate TTPs.
Why Should Security Teams Use ATT&CK?
I've reiterated this point throughout the article: the primary advantage of the ATT&CK framework is its facilitation of threat-informed defense.
In a previous article, I explored the importance of cyber threat analysis, emphasizing that understanding adversary behaviors is crucial for effective security operations. The ATT&CK framework is a valuable tool for achieving this understanding.
In summary, the ATT&CK framework supports cyber threat intelligence by:
- Providing a foundation for organizations to assess their capabilities and identify gaps.
- Enabling prioritization of detection and analysis, allowing organizations to understand which behaviors they can and cannot mitigate.
- Offering insights into how existing defenses perform against known threats, answering critical questions about the effectiveness of security tools.
By engaging in these practices, security programs can enhance their detection and prevention capabilities, close critical gaps, and ultimately improve their overall defense posture.
The ATT&CK framework is indeed a powerful resource, and I advocate for all SOCs to leverage it for developing robust programs or enhancing existing ones. By utilizing this framework, we can better defend against TTPs and move beyond merely blocking basic IOCs like malicious hashes, IPs, and domains.
For more insights, consider subscribing to my weekly newsletter for the latest articles delivered directly to your inbox!